PrismaWatch is a monitoring solution that is always
there, 24x7, anywhere, anytime, and in any condition.
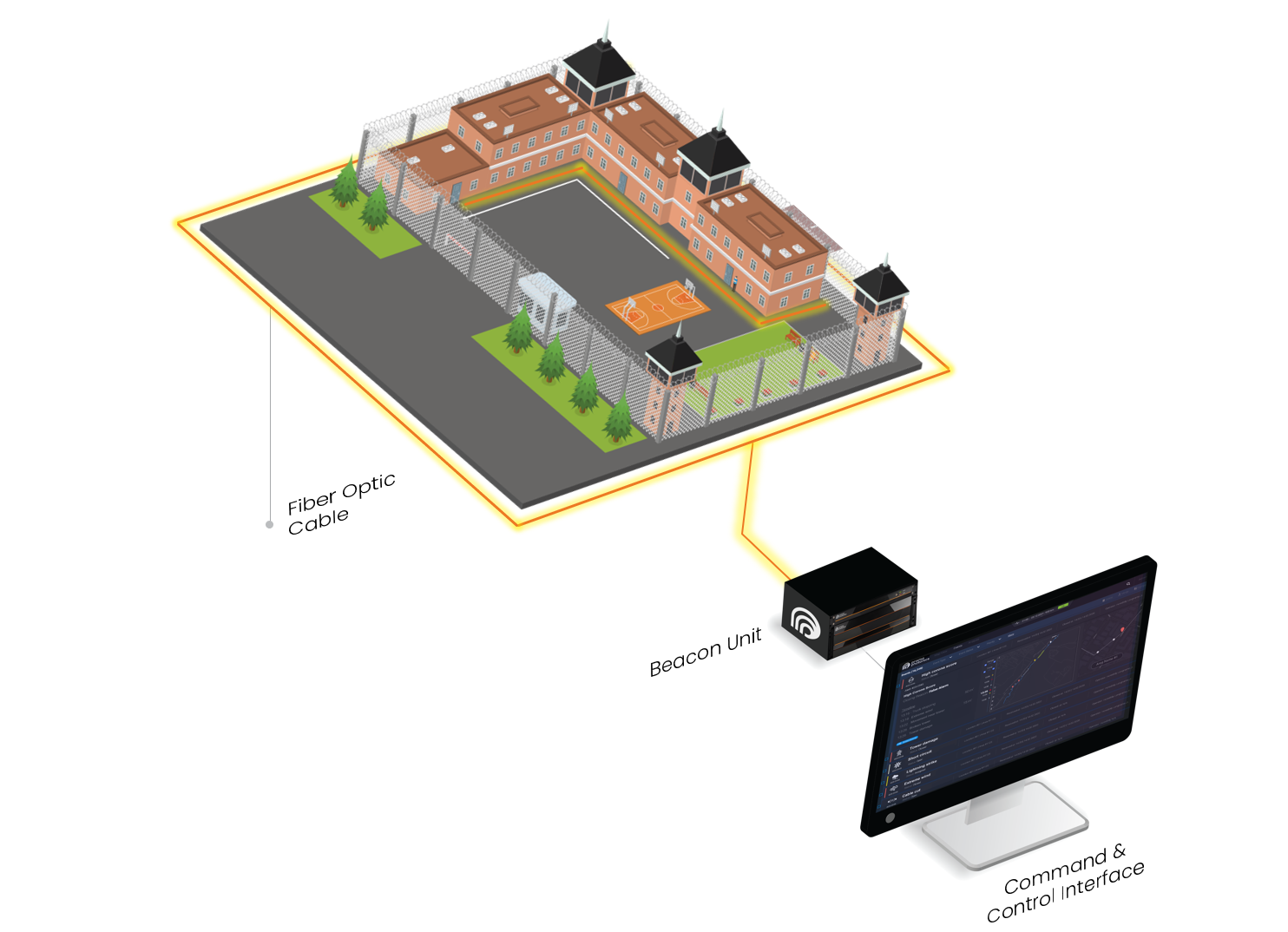
PrismaWatch™ flags suspicious activities and underground threats within the secured compounds. It adds another layer of surveillance, on top of existing security methods, by leveraging a buried optical fiber and without installing extra sensors.
Secured compound operators must detect and identify ongoing, unusual, and suspicious activities within the compound. In parallel, they must deal with smuggling attempts from outside.
PrismaWatch offers dual security from ongoing and real-time threats. It provides an invisible intelligence layer by flagging the facility’s suspicious activities and underground threats. It provides a retrospective analysis of unusual underground activities within the secured compound by tracking the seismic data captured by the optic fiber cables. In parallel, the outer layer delivers real-time alerts, accurately monitoring real-time, fast-occurring threats such as smuggling.
Keeping your facility safe and secure is hard. We know it, and we’re here to help.
Download Brochure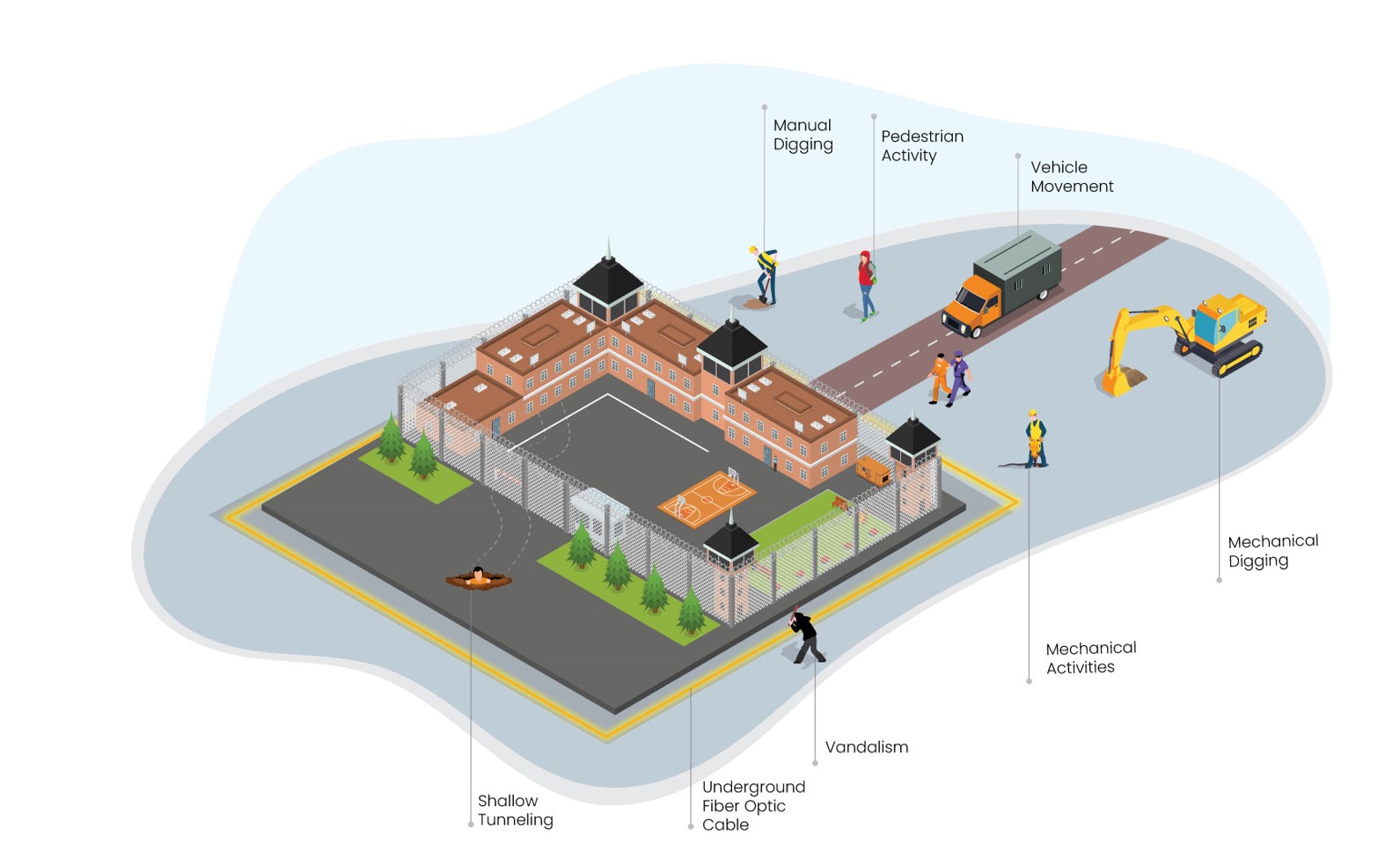
PrismaWatch is effective quickly no need to install extra sensors or cameras, and it’s simply deployed, utilizing a buried optical fiber. The optical fiber is turned quickly into a set of highly sensitive distributed sensors extending around and throughout the facility.
PrimaWatch is operating in two modes at the same time. For continuous activities, a team of experts analyzes the data to identify long, ongoing threats and changes to seismic patterns to point out manual or mechanical digging near and within the perimeter. In a real-time mode, machine learning algorithms take the detailed data collected from the facility to detect events, pinpointing them to meter accuracy as they occur.
Simple deployment
Highly
scalable
Pay as
you grow
Fast time to
response-ability
Accurate & Robust